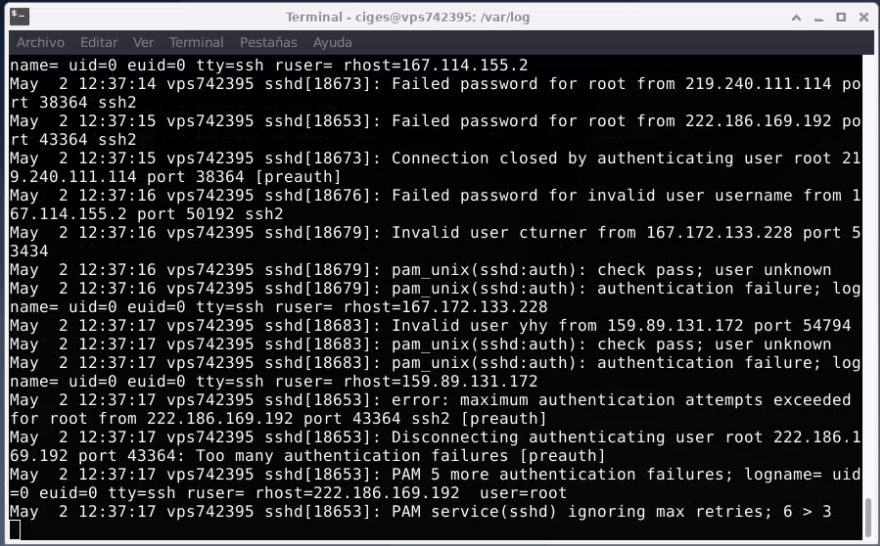
Someone with an automatic tool is trying different combinations of users and passwords to gain SSH access to my public server available in Internet.
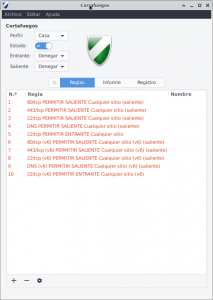
To protect my VPS, I am going to implement some of the recommendations of this post from RimuHosting.
- Run OpenSSH on a non-standard port
- Create a user with a strange name to connect to this server and configure OpenSSH to only allow this user to connect
- Don’t allow passwords to be used. We will use SSH keys to login in our server.